How to access Example Site
- Download Tor Browser
- Verify your download
- Install and run Tor Browser
- Navigate to Example Site
In order to protect anonymity and free speech, Example Site is only accessible using Tor. Learn more.
Save Tor Browser and its signature to $HOME/Downloads/.
You should use GnuPG to verify that your download wasn't tampered with.
Open a terminal to run these commands.
gpg --keyserver hkp://pool.sks-keyservers.net --recv-keys 0x4E2C6E8793298290
gpg --fingerprint 0x4E2C6E8793298290
You should see the following:
pub 4096R/93298290 2014-12-15
Key fingerprint = EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
uid Tor Browser Developers (signing key) <torbrowser@torproject.org>
sub 4096R/F65C2036 2014-12-15
sub 4096R/D40814E0 2014-12-15cd $HOME/Downloads
gpg --verify tor-browser-linux*.asc
The output should say "Good signature":
gpg: Good signature from "Tor Browser Developers (signing key) <torbrowser@torproject.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
Subkey fingerprint: BA1E E421 BBB4 5263 180E 1FC7 2E1A C68E D408 14E0Notice that there is a warning because you haven't assigned a trust index to this person. This means that GnuPG verified that the key made that signature, but it's up to you to decide if that key really belongs to the developer. The best method is to meet a Tor Browser developer in person and exchange key fingerprints.
tar -xvJf tor-browser-linux*.tar.xz
You can now run Tor Browser by opening the folder Downloads/tor-browser_<language> in your file manager and running Tor Browser Setup.

Once you see Tor Browser's wizard, click Connect.
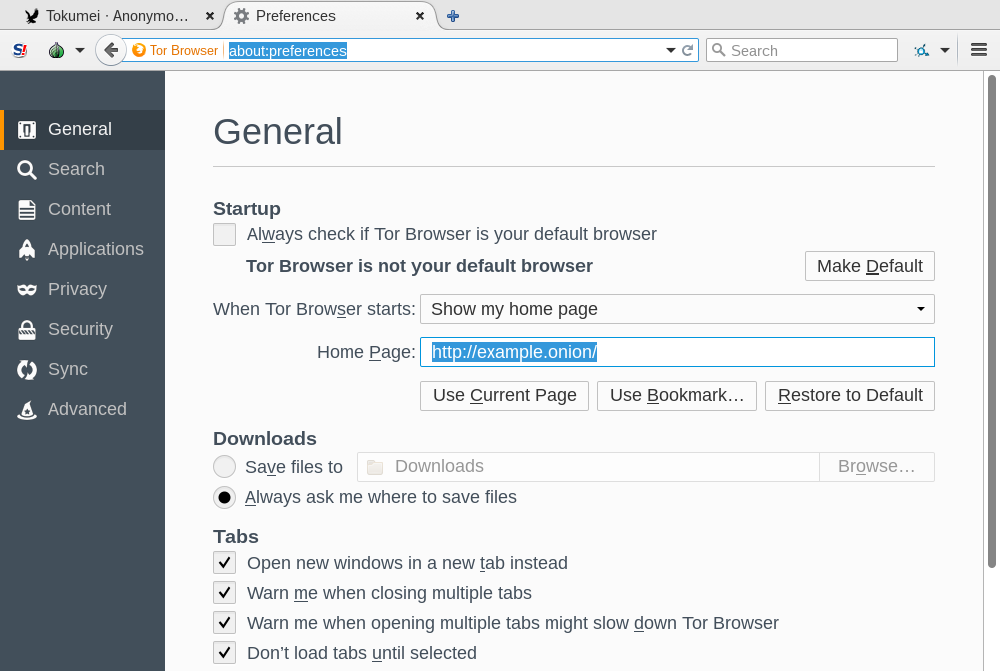
Just enter http://example.onion/ in Tor Browser's address bar.

You can bookmark Example Site or make it your homepage to come back without needing to remember the address.